Managed Security Services
Get 24/7 monitoring, real-time threat detection, and rapid response to protect your enterprise from evolving cyber threats.
* Please note that this hotline is for immediate crisis support only and is not intended to be used for any non-crisis question such as employee inquiries or advertising/marketing/sales solicitations.


Eliminate Security Gaps. Achieve Unified Visibility and Control Across Your Enterprise.
Harness AI to Act on Insights Instantly.
Identify and neutralize threats before they impact your enterprise with real-time AI-powered monitoring and analysis.
Gain centralized visibility and control over your entire security ecosystem, eliminating silos and reducing complexity.
Accelerate response times with intelligent automation that acts on threats instantly, minimizing downtime and impact.
Stay prepared for evolving threats with scalable, cutting-edge technologies tailored for your enterprise's needs.
Simplify your security stack, unlock greater value, and safeguard business continuity. See why industry leaders rely on us.
Detect and mitigate threats before they impact your enterprise.
Accelerate remediation with automated threat analysis and action.
Maximize the ROI of your security investments.
Streamlined processes through AI automation.
Managed Security Services
Get 24/7 monitoring, real-time threat detection, and rapid response to protect your enterprise from evolving cyber threats.
Audits & Response
Identify and address vulnerabilities with in-depth evaluations designed to strengthen your digital defenses and mitigate risks.
Secure Integrations
Optimize and connect your security systems to ensure seamless protection and unified performance across your enterprise.
Digital
Forensics
Expertly investigate and analyze digital evidence, uncovering crucial insights to support legal proceedings, incident response, and ensure the integrity of digital information.
Vulnerability
Assessment
Identify potential security weaknesses, prioritize security risks, and take proactive steps to mitigate those risks before they can be exploited by attackers.
Security
Infrastructure Design
Strategically architect robust systems that safeguard your organization's assets, implementing comprehensive measures to protect against evolving cyber threats.
Red Team
Attack Simulation
Proactively assessing the security of your organization to identify vulnerabilities, test defenses, and enhance your overall cybersecurity resilience.
Our Security Auditing service begins with a thorough assessment of your security landscape, analyzing policies, procedures, and technologies to identify vulnerabilities. We provide actionable insights and recommendations to strengthen your defenses and enhance your overall security posture.
Network Infrastructure Audit
Thoroughly assess your network's architecture, configurations, and security controls to identify vulnerabilities and optimize performance, ensuring a resilient and secure foundation for your business operations in the digital landscape.
Active Directory Audit
Ensure the security and efficiency of your Active Directory infrastructure with a thorough examination, identifying vulnerabilities, enhancing access controls, and optimizing configurations for robust identity and authentication management.
Virtualization, Backup, and Systems Audit
Conduct a comprehensive evaluation of your virtualization infrastructure, backup processes, and systems configurations to ensure optimal performance, data protection, and disaster recovery readiness, enhancing your IT environment's reliability and resilience.
Email Security
Safeguard your organization's communication channels by implementing robust measures to detect and prevent email-based threats, ensuring the confidentiality, integrity, and authenticity of your sensitive information and preventing unauthorized access.
Our intelligent problem-solving approach delivers customized solutions that safeguard critical resources, manage risks, and enable enterprises to thrive in the constantly evolving digital world.
View Insights
In today's digital era, where cyber threats evolve faster than ever, ensuring the security of an organization's digital assets is a necessity.
March 3, 2025
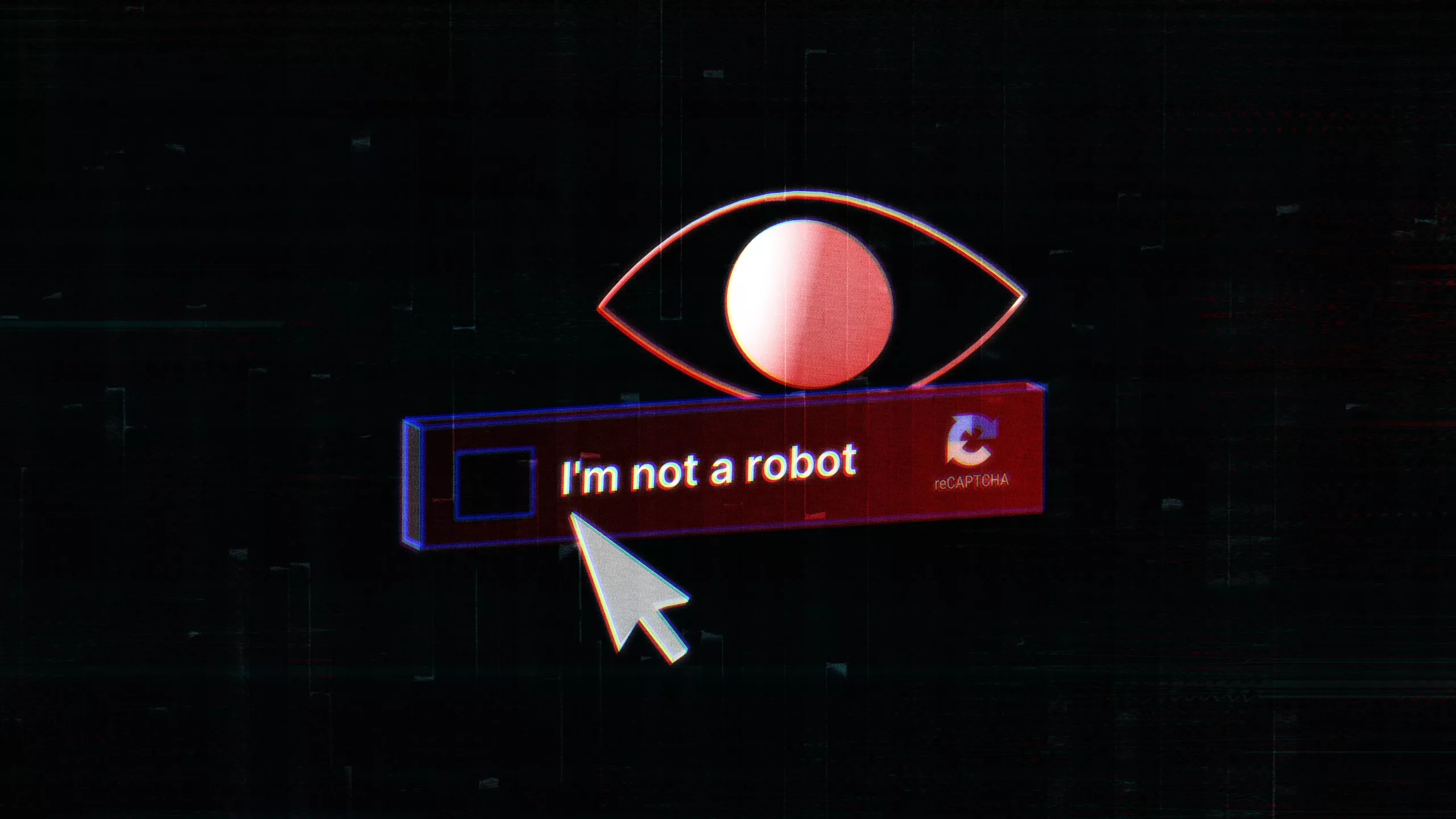
LummaC2 is a stealthy, multi-stage information stealer with advanced infection tactics that target unsuspecting users globally.
November 16, 2024

In a groundbreaking moment for the Maldivian cybersecurity community, OXIQA, in partnership with SentinelOne, hosted the first-ever Capture The Flag (CTF) Challenge in the Maldives.
October 30, 2024

As a cybersecurity company established in the Maldives, we have seen growing trends of organizations facing accidental employee data exposure or information leaks to unauthorized parties.
June 27, 2024